JumpCloud Mobile Device Trust ensures users can access protected resources only from trusted devices. Using a combination of JumpCloud Go™, JumpCloud Device Management, JumpCloud Protect®, and Conditional Access Policies (CAPs), you can safeguard access to protected SSO apps on mobile devices. This article covers how to prepare your org to start using JumpCloud Go for Mobile and Mobile Device Trust on Apple and Android devices.
To configure Device Trust, first enable JumpCloud Go in the Admin Portal. Next, set up JumpCloud Device Management. Depending on your environment, this will require Apple MDM, Android EMM, or both. When your devices are enrolled and managed in JumpCloud, then use Software Management to deploy the JumpCloud Protect app to your devices. Finally, to enforce Device Trust, create a CAP in the Admin Portal to enforce rules around trusted devices.
Prerequisites:
- You’ve reviewed Get Started: Mobile Device Trust and are familiar with the prerequisites and considerations of JumpCloud Go for Mobile and Mobile Device Trust.
Considerations:
- For mobile devices to complete JumpCloud Go for Mobile registration and be considered trusted, they must meet the following conditions:
- Devices are enrolled in JumpCloud Device Management: Apple MDM and/or Android EMM.
- JumpCloud Protect is deployed to devices using Apple VPP and/or Android Software Management.
- JumpCloud Protect evaluates devices and they must pass integrity and jailbreak detection checks. Otherwise JumpCloud Go registration will fail.
- For instructions on how users can prepare their mobile devices and access resources, see Users: Configure Device Trust on Apple iOS and Android Devices.
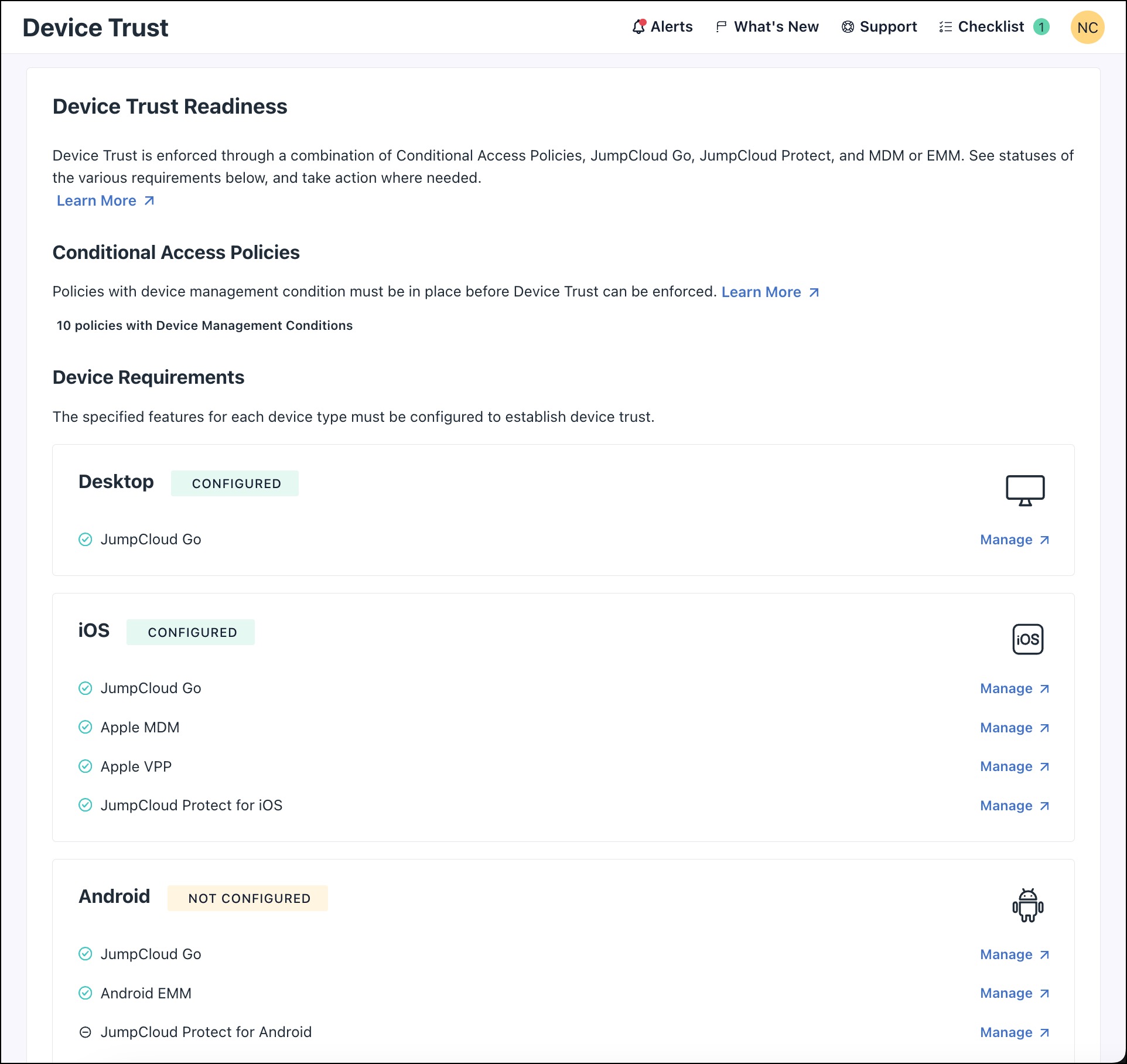
Accessing Device Trust Readiness
The Device Trust Readiness page displays if your org is ready to start using Mobile Device Trust. Configure these prerequisites first before enforcing Device Trust via Conditional Access Policies.
To access Device Trust Readiness:
- Log in to the JumpCloud Admin Portal.
- Go to SECURITY MANAGEMENT > Device Trust.
- Under Device Requirements, review a list of prerequisites for each device type.
- If the prerequisite is configured, a ✅ appears next to the feature name.
- If the prerequisite is not configured, click Manage to open a new tab to the appropriate feature in the Admin Portal and configure it.
You only need to configure the device types used in your org. For example, If your org uses only a single platform (Apple iOS) and doesn't use Android devices, you don’t need to configure Android EMM.
Universal Device Requirements
JumpCloud Go
All device types (Desktop, Apple iOS, and Android) require JumpCloud Go.
- Enable JumpCloud Go in the Admin Portal. See Enabling JumpCloud Go to learn more.
Apple Device Requirements
To use Mobile Device Trust on Apple devices:
- Enable Apple MDM: To meet the requirements for JumpCloud Go for Mobile and Mobile Device Trust, Apple devices must be enrolled in Apple MDM. To do so, you must enable Apple MDM in your JumpCloud org.
- See Set Up Apple MDM.
- Enable Apple VPP: Required to deploy the JumpCloud Protect app to mobile devices.
- See Setting up VPP.
- Create the JumpCloud Protect App in Apple VPP: Use Apple VPP to manage and deploy the JumpCloud Protect app to managed iOS devices.
- Enroll Apple Devices in MDM: After completing the Admin Portal configuration, ensure your devices are enrolled in MDM:
- For company-owned devices, you need to enroll them in MDM. See Add Company-Owned Apple Devices to MDM with Device Enrollment.
- If users access resources from their personal devices, they can enroll their devices directly from the User Portal without admin intervention using user enrollment (BYOD). See Add Personal Apple Devices to MDM with User Enrollment.
- Bind Users to Mobile Devices: (Company-owned devices only): Devices enrolled using Apple Automated Device Enrollment (ADE) or Admin Portal enrollments require you to bind the user to the mobile device record in JumpCloud. See Bind Users to Devices.
- BYOD Apple devices enrolled using User Enrollment for iOS automatically bind the user to the device during enrollment if initiated via the User Portal.
- BYOD/User Enrolled Apple devices require Managed Apple IDs (MAIDs) to enroll in MDM. See Add Personal Apple Devices to MDM with User Enrollment to learn more.
- Browser Requirements: Safari is the recommended browser for JumpCloud Go registration. If another browser is set as the default, users may need to set the default browser as Safari to complete registration.
JumpCloud Protect iOS App
When you deploy JumpCloud Protect app to Apple devices, the user configuration process varies depending on the device and enrollment type:
- Automated Device Enrollment (Company-owned): JumpCloud MDM can silently push a managed instance of JumpCloud Protect or silently take over a personally installed version of JumpCloud Protect.
- Profile-driven Device Enrollment (Company-owned): JumpCloud MDM can push a managed instance of JumpCloud Protect or take over a personally installed version of JumpCloud Protect, but will prompt users to approve.
- User Enrollment (BYOD): JumpCloud MDM can push a managed instance of JumpCloud Protect and prompt users to approve. However, if users already have a personally installed version of JumpCloud Protect, users can delete the existing app to deploy it via MDM, or you allow users to use the existing JumpCloud Protect app on their devices.
If you've enabled JumpCloud Go in the Admin Portal and have iOS devices enrolled, these devices receive a Single Sign-On Extension (SSOE) profile silently. This SSOE profile allows the JumpCloud Protect app to invoke the JumpCloud Go experience for appropriate URLs and managed apps.
Android Device Requirements
To use Mobile Device Trust on Android devices:
- Enable Android EMM: To meet the requirements for JumpCloud Go for Mobile and Mobile Device Trust, Android devices must be enrolled in Android EMM. To do so, you must enable Android EMM in your JumpCloud org.
- See Set Up Android EMM.
- Enable Android Software Management: Enabling Android EMM automatically enables Android Software Management, so no additional configuration is required.
- Create the JumpCloud Protect App in Android Software Management: Use Android Software Management to manage and deploy the JumpCloud Protect app to Android devices.
- See Adding Android Apps.
Additional configuration is required to use the JumpCloud Protect app for Mobile Device Trust on Android devices. Jump to JumpCloud Protect Android App.
- Enroll Android devices in Android EMM: After completing the Admin Portal configuration, ensure your Android devices are enrolled in EMM:
- For company-owned devices, you need to enroll them in EMM. See Enrolling a Company-Owned Android Device to learn more.
- If your users access resources from their personal devices, they can enroll their devices directly from the User Portal without admin intervention using user enrollment (BYOD). See Enrolling a Personal Device to learn more.
- Bind Users to Mobile Devices: (Company-owned devices only): Devices enrolled using Android Zero Touch or Admin Portal enrollments require you to bind the user to the mobile device record in JumpCloud. See Bind Users to Devices.
BYOD Android devices enrolled using the Work Profile automatically bind the user to the device during enrollment if initiated via the User Portal.
- Browser Requirements: Managed Google Chrome is required for JumpCloud Go registration. You must deploy Google Chrome to devices using Android Software Management. Ensure your users are aware of the managed Google Chrome app and that they can download it from the Managed Google Play Store.
- See Adding Android Apps.
JumpCloud Protect Android App
You'll need to configure the JumpCloud Protect Android app in Software Management to use it with Mobile Device Trust.
To configure the JumpCloud Protect app for Android:
- Go to DEVICE MANAGEMENT > Software Management. Select the Google tab.
- Select the JumpCloud Protect app.
- In the Details tab, select Configuration.
- Under Managed configuration, configure the following settings:
- Enter a name in the Configuration name field.
- The OrgID and SystemID values should be prefilled.
- Click Save.
Use the Install Mode to configure the app to force install on the user’s device/work profile, or be available in their Managed Google Play Store for users to manually install.
Configuring Conditional Access Policies (CAPs)
After configuring all the necessary features in JumpCloud for Mobile Device Trust, use CAPs to enforce Device Trust.
- Create a CAP using the Device Management condition to enforce Device Trust and guard appropriate resources.
- Optionally, use the Operating System condition for granular targeting of platforms, for example Android or Apple iOS / iPad OS devices. See Configure a Conditional Access Policy to learn more.

 Step 1
Step 1